Чому зламують сайти і як це впливає на SEO
В інтернеті мене знають як практикуючого SEO-фахівця з Росії. І коли мова заходить про безпеку сайту, то звично всі починають думати про зовсім інші терміни на зразок “IT-SEC” або “ІБ”, а у деяких і зовсім виникають асоціації з антивірусними компаніями. Але якщо Ви з тієї самої категорії людей, то розширю ваш кругозір, бо безпека сайту безпосередньо впливає на результати SEO.
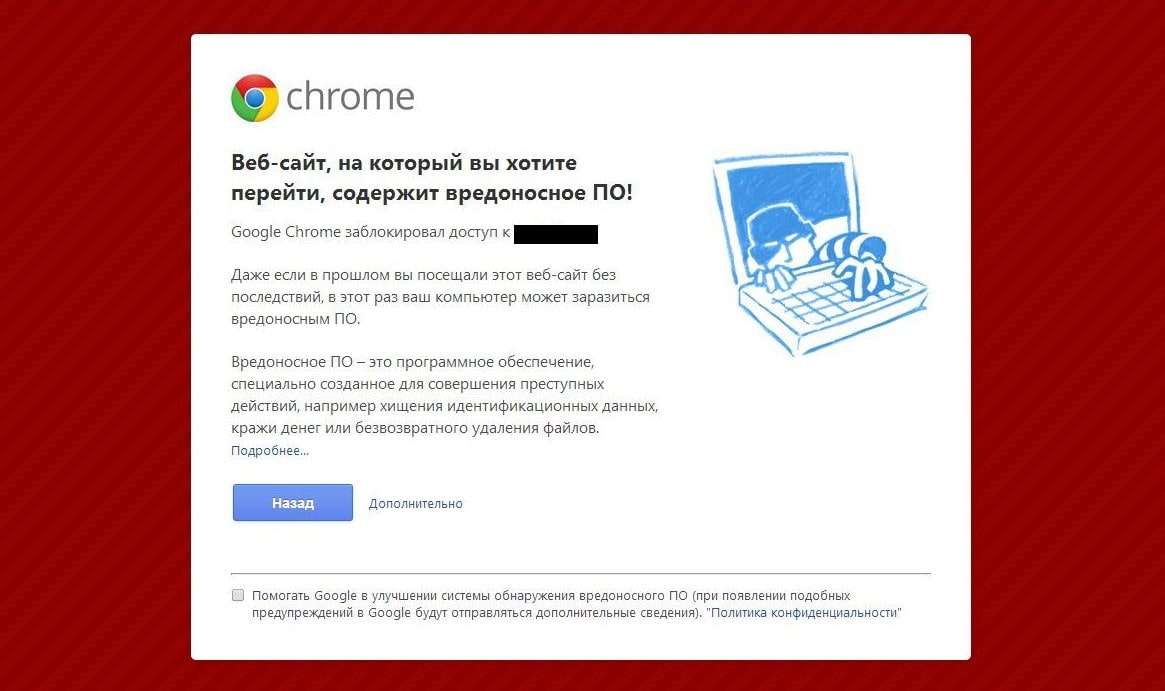
Припустимо, що Ваш сайт заразився вірусом і став недоступний для користувачів, тоді пошукова система через короткий час прибере Вас з ТОП’а. Але частіше відбувається так: якщо ваш сайт заразився вірусом, то пошукова система позначає його як потенційно небезпечний веб-ресурс, який може завдати шкоди користувачеві та відповідно знижується у видачі (або зовсім викидає з SERP). Тобто, зараження сайту вірусами безпосередньо впливає на результати SEO це важливо розуміти.
Чому пошукова система позначає сайт як потенційно небезпечний або шахрайський?
За останні кілька років особистих спостережень я помітив, що зловмисники заражають (найчастіше комерційні) сайти з метою крадіжки конфіденційних персональних даних: скани паспортів, серійні номери продуктів, платіжну та банківську інформацію користувачів.
Але як і раніше зустрічається і таке, що зловмисник зламує сайт лише для того, щоб використовувати потужності сервера для своїх корисливих цілей. Наприклад:
- cпам-розсилка;
- побудова дорвейної сітки;
- бот-мережі;
- створення сайту прокладки для перегону трафіку.
При цьому сам сайт для них не представляє цінності. Отже – це повинно розвіяти міф: “Якщо мій веб-сайт не просувався, не має беклінків і взагалі з поганим дизайном і нікому невідомий, то він не представляє інтересу для злому”.
Третій варіант далеко не рідко зустрічається – злом “жирних” високотрастових сайтів з метою продажу або розміщення власних посилань.
Як ламають і зламують наші сайти
Переважній більшості людей здається, що їх сайти зламують хакери. Від частини це так, але сам хакер приймає вельми непряму участь. Майже завжди злом сайтів відбувається в автоматичному чи напівавтоматичному режимі за допомогою експлойт-китів. Розберімося з термінологією.
Експлойт (Exploit) – це вразливість на сайті, яку можна експлуатувати. За рахунок експлуатації уразливості хакер отримує доступ до сайту або сервера або все відразу.
Експлойт-пак (Exploit Pack) – зібраний набір вразливостей відомих хакеру в одну купу.
Експлойт-кит (Exploit Kit) – програмний модуль, що дозволяє в автоматичному режимі з бази знань (з наявного експлойт-пака) послідовно перебирати і застосовувати до сайту жертви експлойти.
За допомогою такого набору інструментів хакер шукає вразливі сайти по всьому інтернету, і як правило кількість зламаних сайтів сягає від кількох сотень до кількох десятків тисяч штук. Створенням експлойт-паків в основному займаються хакерські угрупування з наступним їх перепродажем на чорному ринку. У своїй практиці я ніколи не зустрічав, щоб їх купували компанії з інформаційної безпеки для проведення своїх лабораторних робіт пентеста (аудит на проникнення).
Які бувають види атак:
XSS – міжсайтовий скриптинг, експлуатує незахищені форми і динамічні скрипти на сайті.
SQL-inject – ін’єкції SQL коду з метою експлуатації бази даних.
PHP-including – впровадження через незахищений РНР-сценарій власний код на РНР.
CSRF – отруєння кеша домену.
Тут перераховані основні типи атак, які підтримують експлойт-паки.
Крім цього є і безліч інших атак: DDoS, фішинг, соціальна інженерія. Але ці атаки складніші та вимагають від хакерів реальних рухів тіла. Для здійснення таких атак у зловмисника повинна бути реальна мотивація, щоб нашкодити. Вам слід боятися якщо Ви – комерційний банк, великий агрегатор або інтернет-магазин, ігровий сервер і т.д.
Як дізнатися що сайт зламаний?
Але якщо Ви все ж не банк, то як же дізнатися що ваш сайт зламали? Іноді це помітно відразу:
- Ваш сайт перестав працювати (часто видає 500 помилку);
- Ваш сайт став вкрай повільно працювати;
- Дефейс сайту (Deface – зміна головної індексної сторінки вашого сайту на сторінку хакера);
- Частина функціоналу сайту перестала працювати;
- Сайт часто падає в 502 помилку;
- Вас не пускає в адмінку.
Іноді буває так, що видимих симптомів немає, але якщо ви зайдете на свій сайт через FTP або подивіться через файловий менеджер (сPanel, Plesk, ISPmanager, DirectAdmin), то можете виявити незнайомі файли, яких раніше не було. Як правило вони містять зашифровані інструкції, частина коду взагалі може бути обфусцірована і так само зашифрована.
Марно займатися SEO просуванням сайту поки він заражений шкідливими скриптами.
Можна спробувати прийняти жалюгідну спробу власноруч або в автоматичному режимі видалити всі ці файли з сумнівним вмістом, але через короткий час вони з’являться знову. При цьому варто відзначити, що “рідні” файли Вашої CMS так само можуть бути заражені, в них органічно впроваджений чужий код і без знань РНР буває складно розібратися що є що.
Така ситуація знайома багатьом, навіть досвідчені вебмайстери впадають в замішання. Добре якщо тарифний план Вашого хостингу передбачає функцію антивірусного сканування і очищення всього шкідливого ПО, але у багатьох хостерів такого нема дотепер і це реальна проблема.
Антивірусне очищення – це добре, але важливо зрозуміти яким чином стався злам. Тобто потрібно виявити вразливість. Для цього потрібно підняти всі наші журнали з балками і провести ретельний аналіз і виявити в який момент щось сталося незвичайне. На основі цього потрібно поставити “латку” на сайт, щоб подібних інцидентів не повторювались.
Якщо ви використовуєте НЕ самописний CMS, то в більшості випадків підійде своєчасне оновлення всіх використовуваних плагінів, видалення невикористовуваних, оновлення ядра CMS, оптимізація роботи бази даних. Якщо у Вас самописна CMS, то тут підійде як ніколи фраза: “Зверніться до Вашого розробнику”.
Сайти на яких CMS найчастіше зламують
Дотепер в головах людей щільно живе міф, що найчастіше зламують сайти створені на безкоштовних CMS таких як:
- Joomla;
- WordPress;
- MODx
- OpenCart
- і т.д.
Насправді це велика помилка. Платні CMS так само активно зламують, якісь більше, якісь менше. Все залежить від команди підтримки цієї CMS, від її оперативності знаходити і закладати уразливості. У безкоштовних CMS цим переважно займається спільнота.
Виробники CMS (особливо Bitrix) люблять говорити, що їх CMS найбільш захищена, але насправді ідеального захисту не існує і при великому бажанні ламається абсолютно все. Так, можна захиститися від ботів працюючи у зв’язці з експлойт-паком, але якщо Вас вирішили цілеспрямовано зламати люди (хакери), скоріше за все це відбудеться.
Висновок:
Швидше за все Ви не банк і не велика корпорація, що веде торговельні справи з усім світом, і Ви мало кому цікаві. З імовірністю 99% Ваші малоцікаві сайти будуть ламати боти і реальному хакеру до Вас немає ніякого діла. Захиститися від ботів можна шляхом своєчасного оновлення ядра CMS і плагінів, якщо у Вас VPS / VDS, то уповаємо на Вашого системного адміністратора, а так всі інші питання можна вирішити за технічною підтримкою хостингу.
Якщо у Вас багато конкурентів, що бажають Вам “смерті”, є ймовірність, що вони викладуть кругленьку суму грошей хакеру для проведення точкових атак (наприклад DDoS) на ваш сайт. В такому випадку слід спочатку подбати про свою безпеку ще на стадії вибору хостингу. Рано чи пізно конкуренти зрозуміють, що їх затія просто не рентабельна.
Автор статті: Роман Бондар
Займаюся SEO просуванням сайтів з 2011 року. Співвласник маркетингової компанії IMarketing (Казахстан). Автор багатьох статей з ефективного лінкбілдінгу і нестандартного крауд-маркетингу. Практикуючий фахівець інформаційної безпеки веб-сайтів.